Security / DevSecOps
“DevOps practices encourage automation to achieve scale, but security has traditionally been manual, process-heavy and gate-driven — the antithesis of automation, transparency and speed”
- Gartner
While traditional testing methods are based on simulated or scripted discrete requests and responses , ReGrade’s unique holistic approach identifies “zero-day” defects or previously unknown, uncategorized defects and bugs. ReGrade is a unique solution that can find zero-day vulnerabilities both before software code is released and after it is running.
ReGrade can detect zero-day vulnerabilities by previewing what a new version will look like against the prior version with production traffic (predictive approach). The product sees deviations in responses from the new version that could indicate a new vulnerability was introduced in the coding of that version. This is a unique feature to Curtail and can obviate the need for certain bug bounty types of programs.
Similarly, ReGrade can also help verify patches for vulnerabilities by comparing the patched and unpatched versions.
Finally, ReGrade can find zero-day vulnerabilities after release by comparing the just released version to the prior version.
In addition, Curtail’s solution ReCover can find zero-day attacks on software. When an attack is found, ReCover can automatically divert traffic to clean, resilient systems to quickly, safely and reliably maintain business operations at all times.
ReCover

Curtail ReCover proactively detects anomalies, including zero-day attacks, and automatically diverts traffic to clean, resilient systems to quickly, safely and reliably maintain business operations at all times.
3rd Party Supply Chain Security
Detect Supply Chain Security Issues
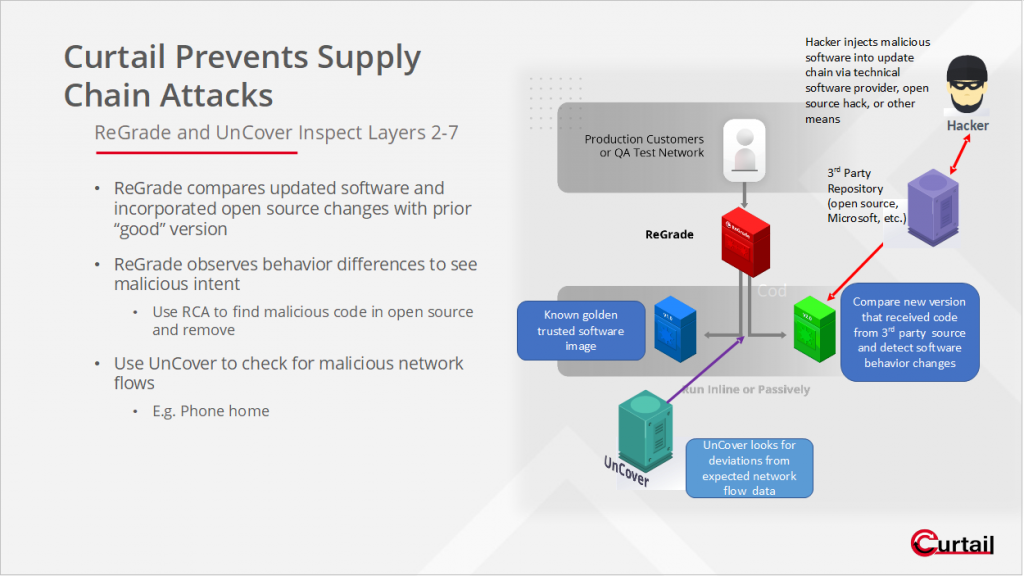
Use ReGrade and UnCover to deal with supply chain security issues especially from 3rd party and open-source repository attacks. Hackers are increasingly finding and an easy vector to compromise corporate software and applications by attacking the open-source or 3rd party software that corporations draw on to write their code. This is pretty much everyone. By compromising 3rd party or open-source software hosted in software registries like RubyGems or npm, hackers can inexpensively break into a corporate network as new software builds and thereby incorporate the hacked software into the corporation’s new code. As many corporations draw on these same 3rd party resources to bring into their code, hackers can now amplify their presence, as this hacked code is quietly and unknowingly absorbed. The “quiet” part is what should scare companies. Once this type of supply chain attack is successful, there is virtually no way to detect the presence of these attackers, especially if they sleep or increase their dwell times before becoming active inside a host network. From inside, they can launch a variety of attacks including ransomware; shutting down systems; corrupting, altering and/or destroying data and critical infrastructure; and stealing information among a variety of problems.
Fight back with NCAST
A new approach to dealing with these problems is called NCAST (Network Comparison Application Security Testing) in which you compare network responses to identify security (zero-day vulnerabilities) or other software development (bugs, misconfigurations, etc.) issues. ReGrade falls in the NCAST category. Use ReGrade to determine whether a version of software had malware injected into it by observing and comparing the behavior of the new version (with the 3rd party code) with the previous “good” or known version.
To supplement ReGrade, you can also use UnCover to look for anomalous network traffic flows which may indicate the presence of a hacker. UnCover forms a statistical baseline of normal traffic and looks for deviations including “phone home,” misconfigured servers, and improper access requests. UnCover collects network flow metadata and compares to historical statistical patterns, identifying and ranking and outliers.